In this post, we will see the required setup for WSS10 SAML policies and we will use SOAP UI to demonstrate client side setup in brief and recommend to refer to previous post for detailed steps to create Outgoing Configuration at client side and server side keystore setup.
SAML Issuer Setup:
wss10_saml_token_service_ policy:
Create an Outgoing Configuration with SAML Token as shown below.
SAML Token:
- SAML Verison: 1.1
- Uncheck Signed
- Assertion Type: Authentication
- Confirmation Method: Sender Vouches
- Issuer: www.oracle.com
- Subject Name: <<username>>
- Subject Qualifier: leave it blank
- Digest Algorithm: http://www.w3.org/2000/09/xmldsig#sha1 (Optional)
- Signature Algorithm: http://www.w3.org/2000/09/xmldsig#rsa-sha1 (Optional)
Attach Outgoing Configuration to request as shown below.
wss10_saml_token_with_message_integrity_service_ policy:
Requires both SAML Token and message body to be digitally signed, hence we need to modify above SAML token setup to consider signing and need to add separate Signature setup in Outgoing Configuration.
SAML Token modification:
Check Signed attribute and use the client side keystore and private key alias as shown below.
Add Signature setup in Outgoing Configuration as shown below.
- Parts
wss10_saml_token_with_message_protection_service_ policy:
Requires to setup SAML Token, Timestamp, Signature and Encryption in Outgoing Configuration where as SAML Token, Timestamp and Body to be digitally signed and Body to be encrypted.
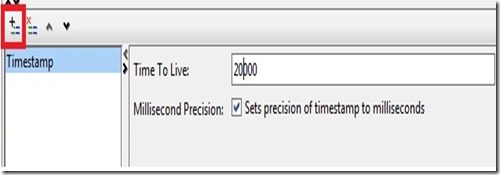
Timestamp:
SAML Token:
- SAML Verison: 1.1
- Uncheck Signed
- Assertion Type: Authentication
- Confirmation Method: Sender Vouches
- Issuer: www.oracle.com
- Subject Name: <<username>>
- Subject Qualifier: leave it blank
Signature:
- Keystore: clientkeystore.jks
- Alias: localclient
- Password: <<keystore password>>
- Key Identifier Type: Binary Security Token
- Algorithm: http://www.w3.org/2000/09/xmldsig#rsa-sha1
- Canonicalization: http://www.w3.org/2001/10/xml-exc-c14n#
- Digest Algorithm: http://www.w3.org/2000/09/xmldsig#sha1
- Check Use single certificate for signing
- Add the below ones in Parts along with correct names and namespaces:
- Body – http://schemas.xmlsoap.org/soap/envelope/
- Timestamp – http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd
- Assertion- urn:oasis:names:tc:SAML:1.0:assertion
Encryption:
- Keystore: clientkeystore.jks
- Alias: localosb
- Key Identifier Type: Binary Security Token
- Symmetric Encoding Algorithm: http://www.w3.org/2001/04/xmlenc#aes128-cbc
- Key Encryption Algorithm: http://www.w3.org/2001/04/xmlenc#rsa-oaep-mgf1p
- Check Create Encrypted Key
- Add the below ones in Parts with correct names and namespaces:
Note: we should maintain the order Signature and Encryption in Outgoing Configuration as shown above.
Attach both Outgoing and Incoming configuration as shown below.
Sample SAML1.1 Assertion:
<saml1:Assertion AssertionID="_14F9EF7DC64266B61B144285601642823" IssueInstant="2015-09-21T17:20:16.428Z" Issuer="www.oracle.com" MajorVersion="1" MinorVersion="1" xsi:type="saml1:AssertionType" xmlns:saml1="urn:oasis:names:tc:SAML:1.0:assertion" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<saml1:Conditions NotBefore="2015-09-21T17:20:16.428Z" NotOnOrAfter="2015-09-21T17:25:16.428Z"/>
<saml1:AuthenticationStatement AuthenticationInstant="2015-09-21T17:20:16.428Z" AuthenticationMethod="urn:oasis:names:tc:SAML:1.0:am:password" xsi:type="saml1:AuthenticationStatementType">
<saml1:Subject>
<saml1:NameIdentifier Format="urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified">weblogic</saml1:NameIdentifier>
<saml1:SubjectConfirmation>
<saml1:ConfirmationMethod>urn:oasis:names:tc:SAML:1.0:cm:sender-vouches</saml1:ConfirmationMethod>
</saml1:SubjectConfirmation>
</saml1:Subject>
</saml1:AuthenticationStatement>
</saml1:Assertion>
Notes:
- With above setup, the request is returning error response when I used SOAP UI5.0.0 but working with SOAP UI 5.2.0. So I would recommend to use SOAP UI 5.2.0.
- Observe that, we had added Assertion as one of the Parts in Signature setup. This is the only option working for Message Protection policy and it’s not working when signing setup is done in SAML Token by checking Signed.
- In SOAP UI, i got the saying Error getting response for […]; null even with all this setup. Following solution is given here to resolve this issue.
Replace the existing xmlsec-1.4.5.jar file in /lib folder with xmlsec-1.5.2.jar.
Replace the existing wss4j-1.6.16.jar file in /lib folder with wss4j-1.6.2.jar.
wss10_saml20_token_service_ policy:
Required setup is similar to wss10_saml_token_service_ policy except that we have to use SAML Token version 2.0 as shown below.
Sample SAML2.0 Assertion:
<saml2:Assertion ID="_14F9EF7DC64266B61B144294396204152" IssueInstant="2015-09-22T17:46:02.041Z" Version="2.0" xsi:type="saml2:AssertionType" xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<saml2:Issuer>www.oracle.com</saml2:Issuer>
<saml2:Subject>
<saml2:NameID Format="urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified">weblogic</saml2:NameID>
<saml2:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:sender-vouches"/>
</saml2:Subject>
<saml2:Conditions NotBefore="2015-09-22T17:46:02.041Z" NotOnOrAfter="2015-09-22T17:51:02.041Z"/>
<saml2:AuthnStatement AuthnInstant="2015-09-22T17:46:02.041Z">
<saml2:AuthnContext>
<saml2:AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:Password</saml2:AuthnContextClassRef>
</saml2:AuthnContext>
</saml2:AuthnStatement>
</saml2:Assertion>
wss10_saml20_token_with_message_protection_service_ policy:
Required setup is similar to wss10_saml_token_with_message_protection_ service_ policy except that we have to use SAML Token V2.0 and have to add the following in Parts of Signature setup. Note the namespace change.
- Assertion urn:oasis:names:tc:SAML:2.0:assertion
wss10_saml_token_with_message_protection_ski_basic256_service_policy:
Similar setup as OWSM policy wss10_saml_token_with_message_protection _ service_ policy except that different Key Encryption, Encoding algorithms and Key referencing mechanism.
Timestamp:
SAML Token:
Signature:
- Keystore: clientkeystore.jks
- Alias: localclient
- Password: <<keystore password>>
- Key Identifier Type: Subject Key Identifier
- Algorithm: http://www.w3.org/2000/09/xmldsig#rsa-sha1
- Canonicalization: http://www.w3.org/2001/10/xml-exc-c14n#
- Digest Algorithm: http://www.w3.org/2000/09/xmldsig#sha1
- Check Use single certificate for signing
- Add the below ones in Parts along with correct names and namespaces:
- Body – http://schemas.xmlsoap.org/soap/envelope/
- Timestamp – http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd
- Assertion- urn:oasis:names:tc:SAML:1.0:assertion
Encryption:
- Keystore: clientkeystore.jks
- Alias: localosb
- Key Identifier Type: Subject Key Identifier
- Symmetric Encoding Algorithm: http://www.w3.org/2001/04/xmlenc#aes256-cbc
- Key Encryption Algorithm: http://www.w3.org/2001/04/xmlenc#rsa-oaep-mgf1p
- Check Create Encrypted Key
- Add the below ones in Parts with correct names and namespaces:
Note: When we use 256-bit encryption algorithm in SOAP UI, we are seeing the error ‘java.security.InvalidKeyException: Illegal key size or default parameters’. This is because java does not support key sizes greater than 128 by default. To get rid of this error, we need to copy policy files local_policy.jar and US_export_policy.jar to %java_home%/jre/lib/security. The policy files can be downloaded using the following links depending on the JDK you use.
Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files 6
Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files 7 Download
Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files 8 Download
SOAP UI can either use your existing JDK installation or bundled JRE and this information can be found in <<SOAP UI Install Dir>>\bin\soapui.bat. If bundled JRE is used by SOAP UI then we need to copy above policy files to location <<SOAP UI Install Dir>>\jre\lib\security.
You can get the SOAP UI project and keystores used in this post over here.

























Hi siva,
I am encountering a problem with wss10_saml_token_with_message_protection_service_ policy.Soap UI is saying “InvalidSecurity : error in processing the WS-Security security header”. The wss10_saml_token_service_ policy and the wss10_username_with_message_protection_ server_policy worked fine for me.
Please could you help.
could you check whether the payload in SOAP UI showing all information like SAML Token, Timestamp, Digital Signature and Encryption
Thanks !! great post!
i test one and one don’t work for me “wss10_saml_token_with_message_protection_service_ policy”
i don’t now what’s wrong with the config in SoapUi.
Did you cross verify ur settings with what mentioned in the post..and whats the error you are seeing.
i see BEA-386200: General web service security error, i copy the same text of the post and check several times and still show the same error.
i really don’t now what’s wrong.
all server side settings also done?