In this post, I will demonstrate required steps at both server and client side for the OWSM policy oracle/wss10_username_with_message_protection_ server_policy. I will use SOAP UI to demonstrate the client side setup.
Server Side
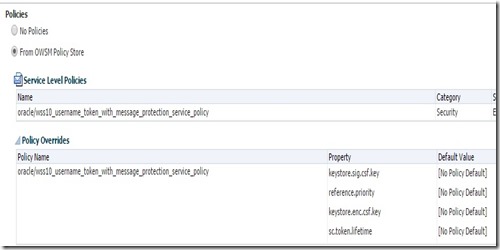
Attach OWSM policy to service, here I will be using OSB Proxy Service for demo.
This OWSM policy requires private keys to be generated at both server and client side. So create clientkeystore.jks for SOAP UI and osbkeystore.jks for server using commands below.
keytool -genkeypair -keyalg RSA -alias localclient -keystore clientkeystore.jks -storepass cljks123 -validity 360 -keysize 2048
keytool -genkeypair -keyalg RSA -alias localosb -keystore osbkeystore.jks -storepass osbjks123 -validity 360 -keysize 2048
Export the public certificate from each keystore using following commands.
keytool -exportcert -alias localclient -keystore clientkeystore.jks -file localclient.cer
keytool -exportcert -alias localosb –keystore osbkeystore.jks -file localosb.cer
Import the certificate into each other using following commands.
keytool -importcert -alias localclient -keystore osbkeystore.jks -file localclient.cer
keytool -importcert -alias localosb –keystore clientkeystore.jks -file localosb.cer
Now add these keys in oracle.wsm.security map using the following steps.
Create key keystore-csf-key as below.
Also create other 2 keys enc-csf-key and sign-csf-key similar to above using the same alias localosb.
Now navigate to the WSM Domain Configuration as shown below to set the keystore and keys to be used by OWSM runtime.
Client Side
The SOAP UI documentation has detailed information related to ws-security setup here so I will keep my description brief and readers are recommended to go through the given link.
Double click on SOAP UI project where we can specify ws-security setup.
Keystores:
Add clientkeystore.jks in Keystores tab and give the key store password as shown below. Status should be shown as OK implies that it’s a valid keystore.
Incoming WS-Security configuration:
Since clientkeystore.jks has required keys for both encryption and digital signature, we have to just select this keystore in Incoming Configuration as shown below.
Outgoing WS-Security configuration:
Add Outgoing Configuration with name OutConfig as shown below.
Now we have to add the configuration for Timestamp, Username Token, Signature and Encryption in detail tabs of Outgoing Configuration as required.
- Timestamp
- Give 20000 as value for Time to live
- Check Millisecond precision
- Username Token
- Give Username and Password
- Check Add Nonce and Add Created
- Select Password Type as PasswordText
- Digital Signature
- Keystore: clientkeystore.jks
- Alias: localclient
- Password: <<keystore password>>
- Key Identifier Type: Binary Security Token
- Algorithm: http://www.w3.org/2000/09/xmldsig#rsa-sha1
- Canonicalization: http://www.w3.org/2001/10/xml-exc-c14n#
- Digest Algorithm: http://www.w3.org/2000/09/xmldsig#sha1
- Check Use single certificate for signing
- Add the below ones in Parts along with correct names and namespaces:
- Encryption
- Keystore: clientkeystore.jks
- Alias: localosb
- Key Identifier Type: Binary Security Token
- Symmetric Encoding Algorithm: http://www.w3.org/2001/04/xmlenc#aes128-cbc
- Key Encryption Algorithm: http://www.w3.org/2001/04/xmlenc#rsa-oaep-mgf1p
- Check Create Encrypted Key
- Add the below ones in Parts section with correct names and namespaces:
Note: we should maintain the order Signature and Encryption in Outgoing Configuration as shown above.
Adding Outgoing/Incoming configuration:
With all this setup in place, when I execute the request I was getting the error saying Error getting response for […]; null. Following is the solution given in one of the forum posts here. Note that, I was using SOAP UI 5.0.0.
Replace the existing xmlsec-1.4.5.jar file in /lib folder with xmlsec-1.5.2.jar.
Replace the existing wss4j-1.6.16.jar file in /lib folder with wss4j-1.6.2.jar.
Sample Request
Sample Response
Note: We also have another way of attaching Outgoing Configuration to the request as shown below by doing right click on request window. When we do this way, don’t select Format XML option on right click which is causing digital signature verification failure.So I always recommend the above mentioned way to attach Outgoing Configuration.
Similarly, for OWSM policy oracle/wss_username_token_service_policy the above Username token setup is enough.
You can get the SOAP UI project and keystores used in this post over here.
























Hi Siva,
Tried executing with “oracle/wss10_username_token_with_message_protection_ server_policy”
but this time I am facing “;Error 401–Unauthorized” issue from SOAP UI (5.2.0) saying
‘The request requires user authentication. The response MUST include a WWW-Authenticate header field (section 14.46) containing a challenge applicable to the requested resource. The client MAY repeat the request with a suitable Authorization header field (section 14.8). If the request already included Authorization credentials, then the 401 response indicates that authorization has been refused for those credentials. If the 401 response contains the same challenge as the prior response, and the user agent has already attempted authentication at least once, then the user SHOULD be presented the entity that was given in the response, since that entity MAY include relevant diagnostic information. HTTP access authentication is explained in section 11’
I have applied outgoing configuration in both ways explained above and checked but showing same error
As it is saying authorization issue
I tried to authorize through Message Access Control that is in proxy service under security tab under security settings from predicate list i added my user to get authorized and restarted the servers as well but it still showing the same issue
Kindly help if there is anything we need to apply or check ..!!
In soap ui, did you check the actual request sent in RAW window after applying outgoing configuration… when I tried some of the config are not seen in RAW input some times…
POST http://XXX.yyy.zzz:9003/CALCI_2/ProxyService/calci_ps HTTP/1.1
Accept-Encoding: gzip,deflate
Content-Type: text/xml;charset=UTF-8
SOAPAction: “ADD”
Content-Length: 1246
Host: XXX.yyy.zzz:9003
Connection: Keep-Alive
User-Agent: Apache-HttpClient/4.1.1 (java 1.5)
These are the details I can find in RAW Tab , Authorization is missing
But I am applying it through outconfig. Is there any way to overcome
You have to create the entire configuration again..that’s what i observed..but there may be much more effective soln.. always check your actual request in soap ui to make sure that its applied properly.
1.Policy at Server side : oracle/wss11_username_token_with_message_protection_service_policy
2. I have created two keys with Alias ‘serverKey’ and keystore ‘server.jks’ at server side and with Alias ‘clientkey’ and keystore ‘client_2.jks’
3.Exported certificates and imported them in to one another, placed server.jks under base_domain/config/fmwconfig and restarted the server.
4.Done with the configurations on SOAPUI similar to above described process in blog
5.My service is simple calci service with 4 operations ADD,SUB,MUL,DIV and is working fine with ‘oracle/wss11_username_token_service_policy’ but facing issue with ‘oracle/wss11_username_token_with_message_protection_service_policy’
SOAPUI configuration :
1. For Encryption I have made similar entries under ‘parts’ as mentioned in
blog
Body – http://schemas.xmlsoap.org/soap/envelope/
UsernameToken – http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd
IS this correct or I have to change namespace to ”xmlns:bpel=”http://xmlns.oracle.com/SOA_APP/Project2/BPELProcess1″(namespace of my service)
2.For Signature I have made similar entries under ‘parts’ as mentioned in blog
Body – http://schemas.xmlsoap.org/soap/envelope/
Timestamp – http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd
UsernameToken – http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd
Does this is causing any issue as it is saying
‘Parts or elements to be encrypted according to policy were different from those in the SOAP message.’
Note that the service policy used in the blog post wss10 policy. wss11 policies have some difference in the setup and also use HMAC based signing which free SOAP UI version does not have support for. I suggest you quickly try with wss10 server side policy to make sure that your setup is right at least in that context. And you can search for HMAC usage in SOAP ui in their forums. If you want to try out with wss11 policies try to create proxy in jdeveloper by giving the wsdl for your service.
Hi Siva,
getting below error
Caused by: oracle.wsm.security.policy.scenario.policycompliance.PolicyComplianceException: WSM-00033 : The encrypted message elements or parts do not comply with the policy. The following headers/elements () or attachments () must be encrypted:-
when I have googled the WSM-00033 , I found
Cause: Parts or elements to be encrypted according to policy were different from those in the SOAP message.
Action: Refer to the policy and WS-Security specifications to ensure that all encryption requirements mandated by the policy and the specifications are met.
Level: 1
Type: ERROR
Impact: Security
Unable to resolve kindly help..!!
What’s the policy at serve side… how are you encrypting the required parts at client side while making the request..